In middle of june a new botnet was advertised on underground forum as Upas Kit. (see end of this post for advert). Bot is recognized by Microsoft in Win32/Rombrast familly
 |
| Upas - Login Screen |
 |
| Upas - Map |
 |
| Upas - Bots |
 |
| Upas - Statistics - Bots Online |
 |
| Upas - Statistics - Online Bots |
 |
| Upas - Statistics - Arch |
 |
| Upas - Statistics - Countries |
 |
| Upas - Statistics - Comparing months |
 |
| Upas - Statistics - Spreading |
 |
| Upas - Statistics - Bots Summary statistics |
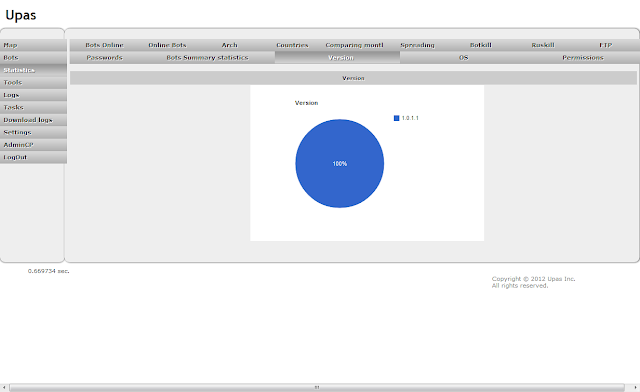 |
| Upas - Statistics - Version |
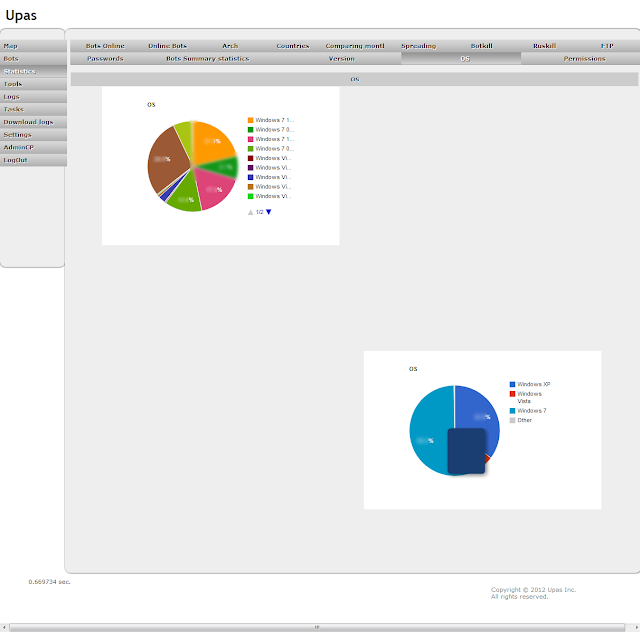 |
| Upas - Statistics - OS |
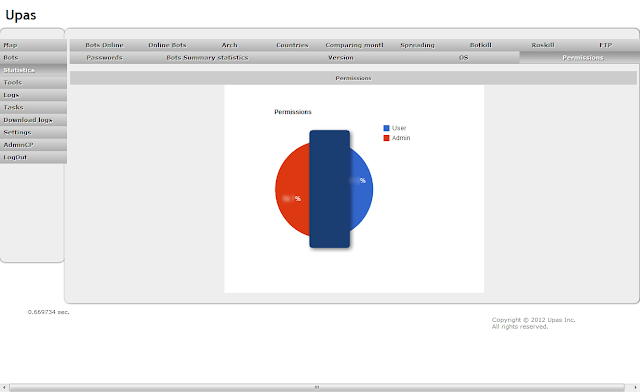 |
| Upas - Statistics - Permissions |
 |
| Upas - Stats |
 |
| Upas - Logs - FTP |
 |
| Upas - Logs - Spreadings |
 |
| Upas - Logs - Botkill |
 |
| Upas - Logs - Passwords |
 |
| Upas - Logs - Ruskill |
 |
| Upas - Logs - Injects |
 |
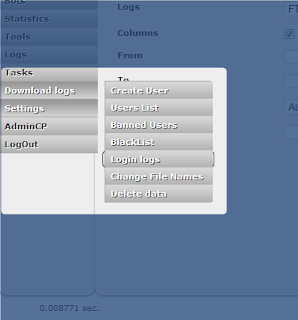
| Upas - Tasks |
 |
| Upas - Public Link to tasks |
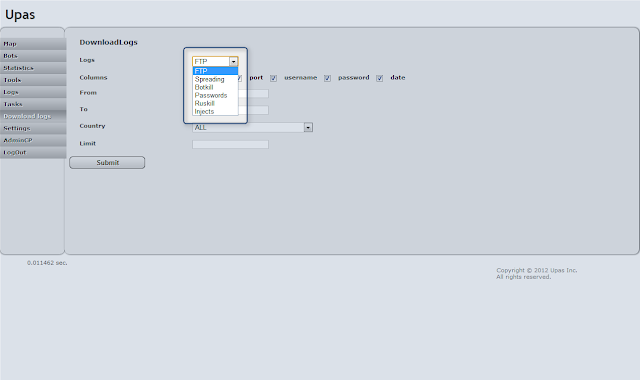 |
| Upas - Download logs |
 |
| Upas - Settings list |
 |
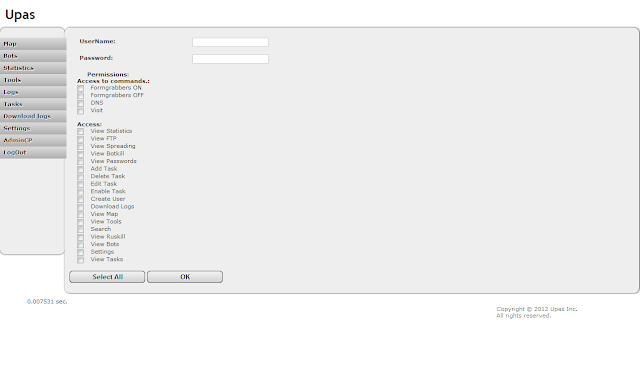
| Upas - Settings |
 |
| Upas - Settings - Create user |
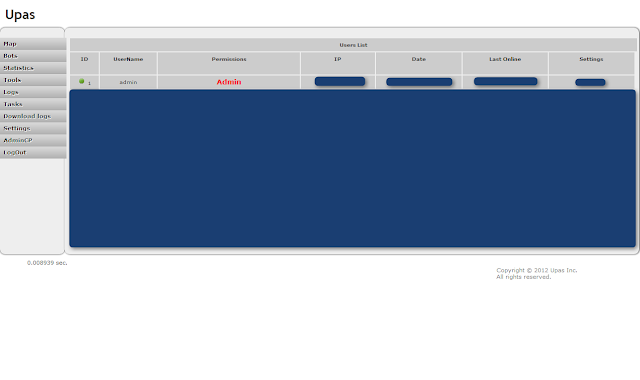 |
| Upas - Settings - Users list |
 |
| Upas - Settings - Banned Users |
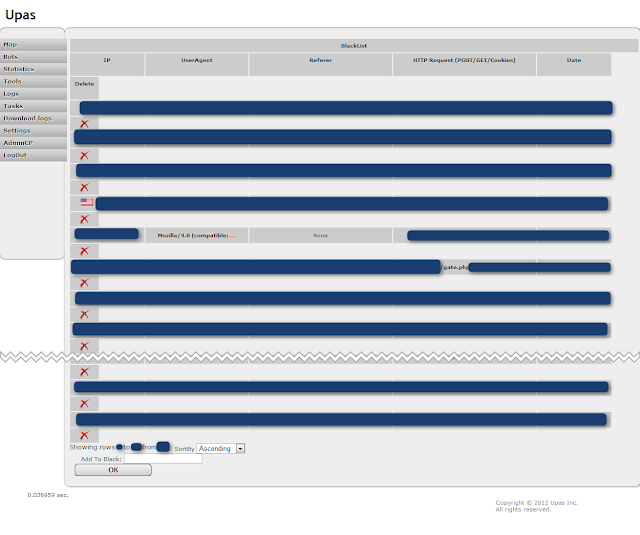 |
| Upas - Settings - Blacklist |
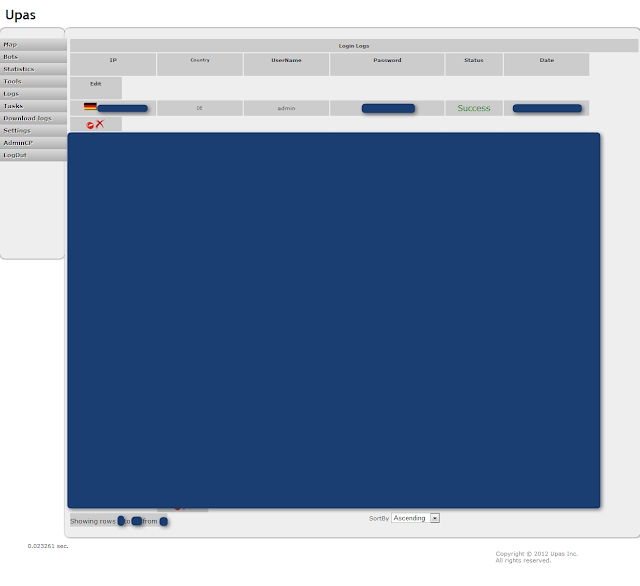 |
| Upas - Settings - Login logs |
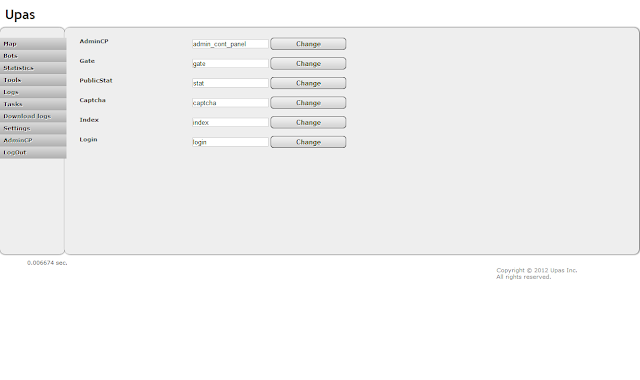 |
| Upas - Settings - Change files name |
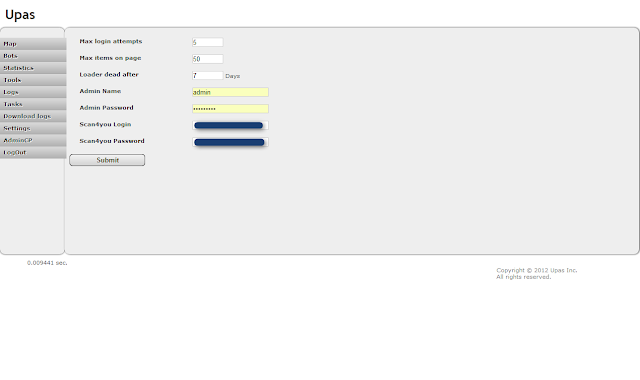 |
| Upas - AdminCP |
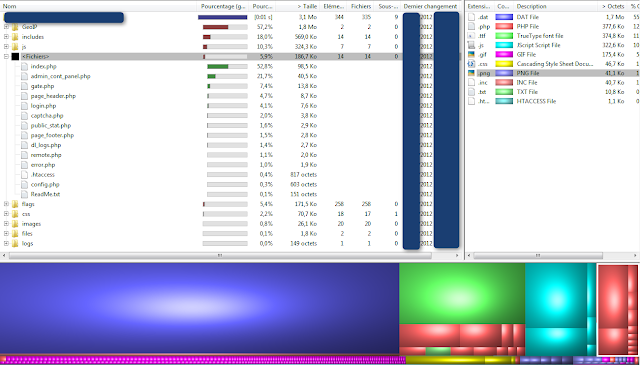 |
| Upas - Server Side Tree |
Here is the initial advert on Exploit.In :
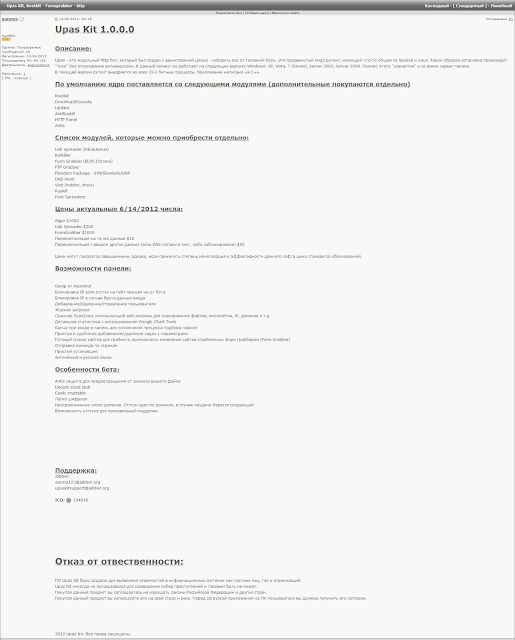 |
| Upas Kit 1.0.0.0 as adverted by auroras on Exploit.in on the 14th of june 2012 |
You'll find the Original text of this advert here :
And its Google Translation here :
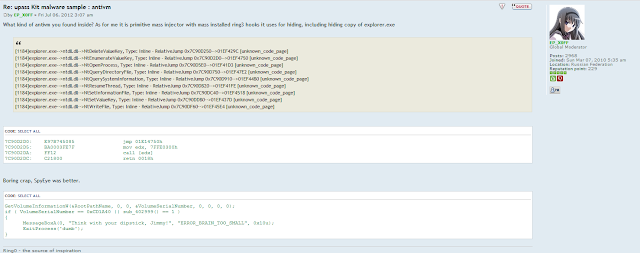 |
| AntiVM analysis by EP_X0FF: |
You'll find it here :
Auroras "reply" on this code :
Which mean he did that fast to escape ThreatExpert. And it looks like it's pretty effective :
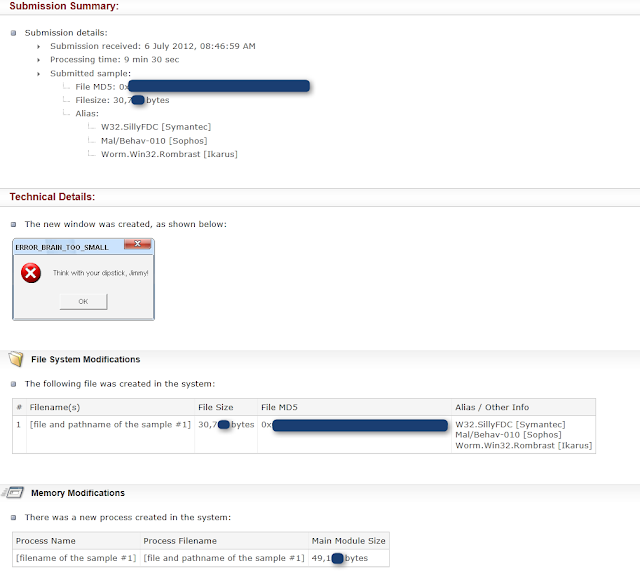 |
| Auroras 1 - ThreatExpert 0 |
For an analysis of Upas kit bot you can take a look at Onthar's post.
(no..these are not bots of the C&C shown here ;) )

