Around 2013-04-27 the prolific "Reveton" Cool EK suddenly became silent. The Ransomware was then pushed in SofosFO and Sweet Orange.
At end of may another Cool EK appeared, operated by another group and with some code that looks like older than last seen version (could be source leak/sell/share). Domains in .us or .pw and path in /blogs/ & /more/.
 |
| /more/ - /blogs/ Cool EK (end of May 2013 - beg of June 2013) |
That one was not widely spread hence not really easy to catch.
Since 10 days a new one appeared. Pushing reveton, many IP, same kind of domain name than THE cool EK.
 |
| Reveton Cool EK back in town - Here 2013-06-25 |
 |
| That Cool EK on URLQuery |
 |
| That Cool EK on Malekal DB. |
Four days ago Chris Wakelin spotted some updates.
Finding a solid Referer I decided to take a look at it.... I first tried Lady Boyle (I miss her) but :
CVE-2013-1493 :
 |
| CVE-2013-1493 Path in Cool EK 2013-06-30 - e=11 |
GET http://neuronapodziemie.containmentmat .com:754/exception-field-assure.php
200 OK (text/html)
Surprise !! Yahoo Trends on the landing...that's known stuff !
 |
| Cool EK and Styx Landing Side to Side - 2013-06-30 |
 |
| All the code (here you see only 10%) is almost exactly the same |
GET http://neuronapodziemie.containmentmat.com:754/nobody_reliance.html
200 OK (text/html)
 |
| "nobody-reliance" decoded |
200 OK (text/html)
GET http://neuronapodziemie.containmentmat .com:754/behalf_political_wheat-boring.html
200 OK (text/html)
 |
| "behalf_political_wheat-boring"decoded |
200 OK (text/html) (call for the jar)
GET http://neuronapodziemie.containmentmat.com:754/loudly-ending_mix.jar
200 OK (application/java-archive) 511c1a7f6b361b0ca1145aef3a2ac2fb (CVE-2013-1493)
GET http://neuronapodziemie.containmentmat.com:754/loudly-ending_mix.exe?e=11
200 OK (application/x-msdownload) e8bf637022b7c010dcf300faaaffac0b
Dll entry : FG00 or XFG00C&C call on 37.139.53.199 & 169 - 67.215.65.132
 |
| Piece of the Reveton Design for France - 2013-06-30 |
 |
| Cool and Styx - CVE-2013-1493 pass Side to Side - 2013-06-30 |
From what we saw we can already draw the graph of exploitation but i'll keep it for the end.
CVE-2013-0431 :
 |
| CVE-2013-0431 pass - Styxy Landing, SofosFOish Exploitation (payload encoded) |
 |
| Piece of CVE-2013-0431 in SofosFOish jar of Cool EK |
CVE-2013-2423:
 |
| CVE-2013-2423 in "Styxy" Cool EK - e=12 |
 |
| jnlp for CVE-2013-2423 jar call |
 |
| Part of CVE-2013-2423 in the SofosFOish Jar of Cool EK |
 |
| CVE-2011-3402 - e=16&h32 |
 |
| Payload URL as Parameter in Cookie |
jZGRH (in Choose-convenient_annually-worthwhile) is a parameter to feed the function that create a Cookie for Duqu like Font Drop path |
CVE-2010-0188 (with CVE-2011-3402 attempt):
 |
| CVE-2010-0188 - e=3 |
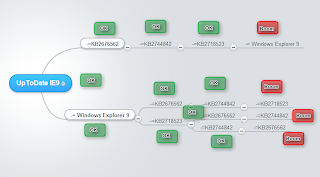
And here is the
Exploitation Graph :
 |
| "Styxy" Cool EK Exploitation Graph - 2013-06-30 |
For CVE-2011-3402 see :
 |
| CVE-2011-3402 try back in october was like that. IE10 and some new patch could also protect you |
Note : no more Flash exploit (for now at least), no x64 duqu font drop.
We could almost name it Styx...
Server react as Cool EK. Admin interface is quite surely Cool...And quite surely no MongoDB/Git here.
Files :
Styxy_Cool_2013-06-30 (OwnCloud via Goo.gl - 6 Fiddler)
<edit: see FAQ for password />
<edit : s/2493/2423 : thx a lot @SecurityObscurity />
<edit 2013-07-02 : added condition on CVE-2011-3402 infection based on comment />
<edit 2013-07-05 : soc eng added in the Exploitation Graph for Java not vuln - explain the failover on this jar />




