 |
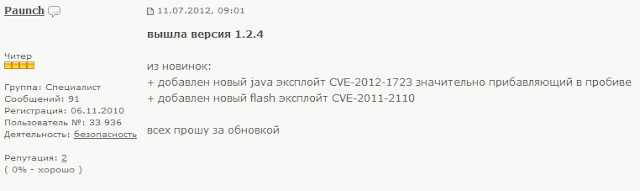
| Paunch Notification on Exploit.In about BH EK 1.2.4 |
----------------------------------------
вышла версия 1.2.4
из новинок:
+ добавлен новый java эксплойт CVE-2012-1723 значительно прибавляющий в пробиве
+ добавлен новый flash эксплойт CVE-2011-2110
всех прошу за обновкой
----------------------------------------
Google Translation :
----------------------------------------
released version 1.2.4
of new products:
+ Added new java exploit CVE-2012-1723 add much to the punching
+ Added a new flash exploit CVE-2011-2110
All I ask for new clothes
----------------------------------------
 |
| BH EK - login Screen (English and Russian + PDA template) |
 |
| BH EK - Statistics |
 |
| BH EK - Threads (Note : Data has been intercepted and modified) |
 |
| BH EK - Files (Note : Data intercepted and modified) |
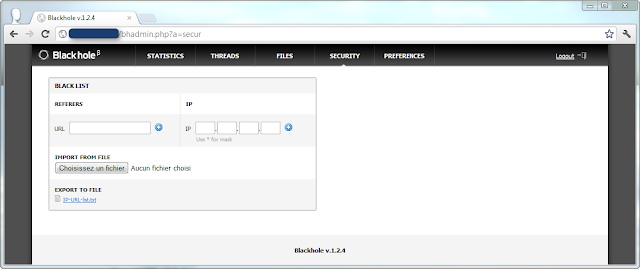 |
| BH EK - Security |
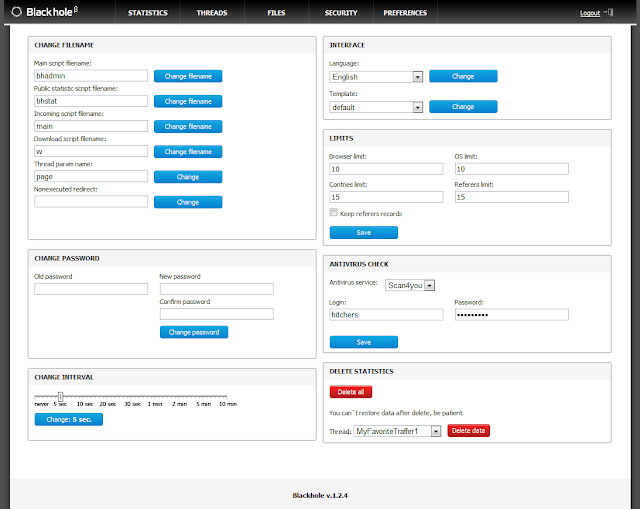 |
| BH EK - Preferences (Note : Data has been intercepted and modified) |
Known exploited vulnerabilities (feel free to comment if some are missing, see at the end for sources) :
CVE-2006-0003 - Unspecified vulnerability in the RDS.Dataspace ActiveX control in Microsoft Data Access Components (MDAC)
CVE-2007-5659 - Multiple buffer overflows in Adobe Reader and Acrobat 8.1.1 and earlier
CVE-2008-2992 - Adobe Reader "util.printf" Vulnerability
CVE-2009-0927 - Stack-based buffer overflow in Adobe Reader and Adobe Acrobat 9 (multiple versions) allows remote attackers to execute arbitrary code
CVE-2009-1671 - Java buffer overflows in the Deployment Toolkit ActiveX control in "deploytk.dll"
CVE-2009-4324 - Adobe Reader and Adobe Acrobat "util.printd" Vulnerability
CVE-2010-0188 - Adobe Acrobat Bundled Libtiff Integer Overflow Vulnerability
CVE-2010-0840 - Sun Java JRE Trusted Methods Chaining Remote Code Execution Vulnerability
CVE-2010-0842 - Java JRE MixerSequencer Invalid Array Index Remote Code Execution Vulnerability
CVE-2010-0886 - Vulnerability in the Java Deployment Toolkit component in Oracle Java SE
CVE-2010-1423 - Java argument injection vulnerability in the URI handler in Java NPAPI plugin
CVE-2010-1885 - Microsoft Help Center URL Validation Vulnerability
CVE-2010-3552 - Sun Java Runtime New Plugin docbase Buffer Overflow (aka "Java Skyline exploit")
CVE-2010-4452 - Sun Java Applet2ClassLoader Remote Code Execution Exploit
CVE-2011-3544 - Vulnerability in the Java Runtime Environment component in Oracle Java SE JDK and JRE 7 and 6 Update 27 and earlier
SpiderLabs talked about
CVE-2011-0611 - Adobe Flash Player before 10.2.154.27 on Windows, Mac OS X, Linux, and Solaris and 10.2.156.12 and earlier on Android; Adobe AIR before 2.6.19140; and Authplay.dll
In march with BH EK 1.2.3 :
CVE-2012-0507 - Unspecified vulnerability in the Java Runtime Environment (JRE) component in Oracle Java SE 7 Update 2 and earlier, 6 Update 30 and earlier, and 5.0 Update 33 and earlier allows remote attackers to affect confidentiality, integrity, and availability via unknown vectors related to Concurrency. (see video & Article from D. Harley at the end of this post)
And now :
CVE-2012-1723 - Unspecified vulnerability in the Java Runtime Environment (JRE) component in Oracle Java SE 7 update 4 and earlier, 6 update 32 and earlier, 5 update 35 and earlier, and 1.4.2_37 and earlier allows remote attackers to affect confidentiality, integrity, and availability via unknown vectors related to Hotspot. (see video & Article from A. Matrosov at the end of this post)
CVE-2011-2110 - Adobe Flash Player Unspecified Memory Corruption Vulnerability
Note Sophos has reported having seen on the thread of a BH EK :
CVE-2012-1889 Microsoft XML Core Services 3.0, 4.0, 5.0, and 6.0 accesses uninitialized memory locations, which allows remote attackers to execute arbitrary code or cause a denial of service (memory corruption) via a crafted web site.
It's maybe not obvious to all readers but in fact BH EK is changing everyday to play his part in the "Poke A Mole" game with Antivirus
 |
| Picture S |
The Java Payload (stage 3 on Picture S) is moving on a daily basis . Here is what i found on a BH EK between June 21 and July 12 :
Note that when they appear it's often a 1 or 2/42 on Virustotal meaning that stage 3 of the Attack will likely work if your software (browser plugins) are not up to date.
If you want to read more about recent move of Blackhole Exploits Kit look this (newer first) :
The rise of a new Java vulnerability - CVE-2012-1723
Jeong Wook - Microsoft Malware Protection Center - 1st Aug 2012
An Examination of Java Vulnerability CVE-2012-1723
Masaki Suenaga - Symantec - 27 Jul 2012
The Rise of the “Blackhole” Exploit Kit: The Importance of Keeping All Software Up To Date
Tim Rains - Microsoft Security Blog - 19 Jul 2012
What did the Java applet say to the SWF? Don't leave me alone in this Blackholeee!
SpiderLabs - 16 Jul 2012
Java the Hutt meets CVE-2012-1723: the Evil Empire strikes back
Aleksandr Matrosov - ESET Threat Blog - 10 Jul 2012
New Java Exploit to Debut in BlackHole Exploit Kits
Brian Krebs - KrebsOnSecurity - 5 Jul 2012
Wham Bam, the Cutwail/Blackhole Combo
Phil Hay - SpiderLabs - 2 Jul 2012
Zero-day XML Core Services vulnerability included in Blackhole exploit kit
Fraser Howard - NakedSecurity (Sophos) - 29 Jun 2012
Java CVE-2012-0507 / CVE-2011-3521
Mila - Contagio - 31 Mar 2012
Blackhole, CVE-2012-0507 and Carberp
David Harley - ESET Threat Blog - 30 Mar 2012
More about CVEs and EK :
An Overview of Exploit Packs (Update 16)
Mila - Contagio - 3 Avr 2012 (Based on François Paget's An Overview of Exploit Packs (McAfee - 28 May 2010) )
